Cybercrime 101: Types of Cybercrimes Every Business Should Understand
Cybercrime is pervasive, and increasingly so in this covid, work-from-home age. According to Cybersecurity Ventures, cybercrime damage is expected to cost the world $6 trillion by 2021. In this article, we will explore the different types of cybercrimes to help you better understand the threats facing your business and your customers’.
What is Cybercrime?
Cybercrime is an umbrella term for an illegal activity that involves a computer, a computer network, or a networked device. Generally, cybercrime is committed with the intent of making money, but this is not always the case. Cybercrime occasionally aims to damage computers for reasons other than profit, possibly a political or personal motive.
Cybercriminals can be individuals or organizations. Some hackers are highly skilled members of an organization, while others are novice lone wolves. And the same is true for cybercrime victims.
Types of Cybercrimes
Malware
Malware, short for malicious software, is essentially a virus. It is a software intentionally designed to damage a computer, server, or computer network. A computer infected with malware can be used by cybercriminals for several purposes: to steal confidential data, to cause damage to data, or to use the computer to carry out other criminal acts.
Within the malware category is ransomware. As the name may suggest, ransomware is a type of malware used to extort money by holding a victim’s data or device to a ransom.
Example: The 2017 WannaCry ransomware attack is one of the most famous and destructive malware attacks in history. Through phishing emails (see below) over 200,000 people, including hospitals, universities, and large corporations, were infected by this harmful software. The losses caused by WannaCry exceeded $4 billion.
Phishing and Social Engineering
Phishing is an attempt by an individual or organization to gain private information, like usernames, passwords, or financial details by tricking a target into divulging this data through a communication (email, instant message, etc) that apparently originates from a widely trusted entity like a bank, company, or web portal. Phishing emails, or communications, are typically sent out en masse. However, spear-phishing messages are targeted phishing campaigns that try to lure individuals into jeopardizing the security of the organization for whom they work.
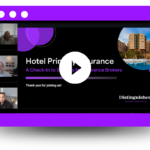
Example: A number of hotels and guesthouses featured on Booking.com have been targeted by phishing emails, resulting in users of the website being sent emails instructing them to provide payment details. Personal customer information, such as names, addresses, phone numbers, costs, reference numbers, and booking dates were included in the email, leading customers to believe that they were legitimate.
Denial of Services
A Denial-of-Service attack (DoS attack) is a cyberattack in which the perpetrator seeks to make a machine or network resources unavailable to its intended users by temporarily or indefinitely disrupting services. DoS attacks overwhelm systems, or flood the targeted machines or resources with requests, in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. DoS attacks may be used to demand money or serve as a diversion while another cybercrime takes place.
Example: Famed global hacking collective, Anonymous launched a DoS campaign to take down the Trump Hotels websites.
How to Protect Yourself Against Cybercrime
Now that you have a better understanding of cybercrime, here are our top tips for protecting yourself:
- Use strong passwords.
- Never open attachments from a sender you do not know.
- Keep your software and operating system up to date.
- Do not click on links in spam emails or unfamiliar websites.
- Contact companies directly about suspicious requests.